
Crack the Swift code for sending international wires

Managing your finances in the military

Real-time treasury: How APIs enable finance teams to unlock legacy data

8 ways for small business owners to manage their cash flow

The latest on cybersecurity: Mobile fraud and privacy concerns

Everything you need to know about changes to Form 8038-CP reporting

What is a home equity line of credit (HELOC) and what can it be used for?

Preparing for retirement: 8 steps to take

How to create a financial plan to grow your LGBTQ+ family

Multiple accounts can make it easier to follow a monthly budget

Estate planning documents: Living trusts vs. will vs. living will

Why estate planning is important

Understanding yield vs. return

Is your financial plan keeping pace with your life?

What type of investor are you?

How a Health Savings Account (HSA) can benefit your retirement plan

How to manage your money: 7 tips to improve your finances

Year-end financial checklist

How to access digital assets after a loved one's death

3 ways to secure purchasing power

Keeping up with an evolving investment industry
Pursue a passion

Celebrate a big event

Travel

Your guide to smart money habits
A stress-free holiday starts now

Guide for investing

Protect yourself from financial exploitation

Financial wellness webinars

The tools you need to make your business boom.
Real Good

3 European market trends to watch

European outlook: Trustee experience more important than ever

U.S. Bank Regulatory Outlook Report | Q4 2022 Edition

U.S. Bank Regulatory Outlook Report 2022 Edition

Trends in economics, immigration and mobility policy

Putting home ownership within reach for a diverse workforce

Emerging trends in Europe: An outlook from multiple perspectives

Rule 18f-4: The limited use exception

Leveraging the ASC-842 rule changes in equipment lease accounting

Housing market trends and relocation impact

Liquidity management: A renewed focus for European funds

How liquid asset secured financing helps with cash flow

Administrator accountability: 5 questions to evaluate outsourcing risks

Blockchain: Separating hype from substance

Hybridization driving demand

The AI journey in finance: How to make it part of your strategy

The ongoing evolution of custody: Tips for renewing your custody contract

IRC Section 305(c): Deemed distributions and related regulations

3 innovative approaches to ESG investing in Europe

Ask an expert Q&A: 3 US ETF trends and their impact in Europe

Rethinking European ETFs: Strategy wrappers and a means to an end

Unique requirements of large private equity firms

Case study: U.S. asset manager expands to Europe

Key considerations for launching an ILP

A first look at the new fund of funds rule

Examining in-demand fund structures

Interval funds find growing popularity

Alternative assets: Advice for advisors

An investor’s guide to marketplace lending

What is a CLO?

What are exchange-traded funds?

MSTs: An efficient and cost-effective solution for operating a mutual fund

For small business growth, consider the international market

6 risks you need to manage when expanding your global footprint

Ask an expert Q&A: 3 US ETF trends and their impact in Europe

Beyond Mars, AeroVironment’s earthly expansion fueled by U.S. Bank

The value of engaging a professional paying and exchange agent

5 tips for a successful joint venture

Know your customer: How updated rules affect M&A closings

Answering the ABL question

Refinancing your practice loans: What to know

ABL mythbusters: The truth about asset-based lending

Finance or operating lease? Deciphering the legalese of equipment finance

Buying or leasing? Questions to ask before signing a contract

What type of loan is right for your business?

Collateral options for ABL: What’s eligible, what’s not?

Can ABL options fuel your business — and keep it running?

Programme debt: 3 IPA lessons learned through experience

5 simple steps for your M&A escrow

How digital platforms streamline client onboarding for investment funds

Alternative fund servicing: bank or boutique?

Mutual fund to ETF conversions: challenges and considerations

Direct lending trends in Europe

The benefit of a multi-jurisdictional European trustee

The role of a custodian

Ask an expert Q&A: automation and artificial intelligence trends in Luxembourg

Investment management platforms: Easily enter the Irish funds market

Ask an expert Q&A: European CLO market outlook

What goes into private equity fund calculation?

Accommodating the growing complexity of private equity funds

Depositary bank and collateral agent

Luxembourg private capital growth demands your attention

Programme debt clients want reliable service – no matter where they’re based

European loan agency: finding the right balance of agility and stability

Custody or safekeeping: What’s the right solution for government investments?

High-yield bond issuance: how to avoid 5 common pain points

Easing complex transactions: Project finance case studies

High-yield bond issuance: 5 traits lawyers should look for in a service provider

Cryptocurrency custody 6 frequently asked questions

Programme debt Q&A: U.S. issuers entering the European market

Luxembourg's thriving private debt market

6 benefits of a multiple-role service model for European funds

Luxembourg funds: 5 indicators of efficient onboarding

Easier onboarding: What to look for in an administrator

ESG-focused investing: A closer look at the disclosure regulation

Maximizing your infrastructure finance project with a full suite trustee and agent

3 questions to ask your equity, quant and CTA fund administrator

4 reasons your Luxembourg fund needs an in-market administrator

Combined strength: Luxembourg and your fund administrator

3 tips to maintain flexibility in supply chain management

Top 3 considerations when selecting an IPA partner

5 questions you should ask your custodian about outsourcing

Insource or outsource? 10 considerations

The secret to successful service provider integration

10 ways a global custodian can support your growth

The reciprocal benefits of a custodial partnership: A case study

The benefits of a full-service warehouse custodian

The unsung heroes of exchange-traded funds

Depositary services: A brief overview

4 questions you should ask about your custodian

Bank vs. brokerage custody

Refining your search for an insurance custodian

Service provider due diligence and selection best practices

Preparing for your custodian conversion

Inherent flexibility and other benefits of collective investment trusts

Webinar replay - The view from Europe: UCITS and ETFs in a changing world

Colleges respond to student needs by offering digital payments

Maximizing your deductions: Section 179 and Bonus Depreciation

6 timely reasons to integrate your receivables

Benefits of billing foreign customers in their own currency

Improve government payments with electronic billing platforms

ABCs of BEC

BEC and deepfake fraud

Third-party vendor risk: protecting your company against cyber threats

Best practices on securing cardholder data

Turn risk into opportunity with supply chain finance

Hospitals face cybersecurity risks in surprising new ways

Authenticating cardholder data reduce e-commerce fraud

Post-pandemic fraud prevention lessons for local governments

Webinar: Robotic process automation

What is CSDR, and how will you be affected?

Risk management strategies for foreign exchange hedging

Proactive ways to fight vendor fraud

Webinar: CRE technology trends

5 Ways to protect your government agency from payment fraud

Avoiding the pitfalls of warehouse lending

Fight the battle against payments fraud

Fraud prevention checklist

Cybercrisis management: Are you ready to respond?

Complying with changes in fund regulations

Why Know Your Customer (KYC) — for organizations

The password: Enhancing security and usability

How to improve your business network security

Government agency credit card programs and PCI compliance

Cybersecurity – Protecting client data through industry best practices

Business risk management for owners of small companies

BEC: Recognize a scam

Evaluating interest rate risk creating risk management strategy

Meeting healthcare strategy goals with electronic patient refunds

Demystifying ISO 20022

Managing cross-border payments in emerging markets

Creating the ideal patient journey

5 reasons to upgrade B2B payment acceptance methods

Take a fresh look: mass transit is going places

Making the cross-border payment decision: Wire or international ACH?

Drive digital transformation with payments innovation

Automating escheatment earns respected innovation award

Why powerful online portals are tailor-made for the public sector

How the next evolution of consumer bill pay makes it easier to do business

Standardizing healthcare payments

Integrated payments healthcare benefits

Consolidating payments for healthcare systems

Role of complementary new channels in your payments strategy

Navigate changing consumer behavior with service fees

Access, flexibility and simplicity: How governments can modernize payments to help their citizens

Modernizing fare payment without leaving any riders behind

Tap-to-pay: Modernizing fare payments pays off for transit agencies and riders

Webinar: Approaching international payment strategies in today’s unpredictable markets.

How real-time inventory visibility can boost retail margins

Escheatment resources: Reporting deadlines for all 50 states

Payment industry trends that are the future of POS

White Castle optimizes payment transactions

ABCs of APIs: Drive treasury efficiency with real-time connectivity

Managing the rising costs of payment acceptance with service fees

Three healthcare payment trends that will continue to matter in 2022

Want AP automation to pay both businesses and consumers?

Webinar: CSM corporation re-thinks AP

Increase working capital with Commercial Card Optimization

How to improve digital payments security for your health system

Banking connectivity: Helping businesses deliver the easier, faster, more secure customer experience of the future

Tech tools to keep your restaurant operations running smoothly

3 benefits of integrated payments in healthcare

Top 3 ways digital payments can transform the patient experience

Automate accounts payable to optimize revenue and payments

Automate escheatment for accounts payable to save time and money

A simple guide to set up your online ordering restaurant

Cashless business pros and cons: Should you make the switch?

ePOS cash register training tips and tricks

Ways prepaid cards disburse government funds to the unbanked

3 reasons governments and educational institutions should implement service fees

Webinar: AP automation for commercial real estate

Understanding and preparing for the new payment experience

Addressing financial uncertainty in international business

Rent payments: What’s changing for commercial real estate

Safeguarding the payment experience through contactless

COVID-19 safety recommendations: Are you ready to reopen?

Higher education and the cashless society: Latest trends

5 winning strategies for managing liquidity in volatile times

3 ways to make practical use of real-time payments

The surprising truth about corporate cards

Instant Payments: Accelerating treasury disruption

The future of financial leadership: More strategy, fewer spreadsheets

How AI in treasury management is transforming finance

Can faster payments mean better payments?

4 benefits to paying foreign suppliers in their own currency

Digital banking and cloud accounting software: How they work together

4 ways Request for Payments (RfP) changes consumer bill pay

Restaurant surveys show changing customer payment preferences

Unexpected cost savings may be hiding in your payment strategy

Transition to international ACH

Digital trends poised to reshape hotel payments

Enhancing the patient experience through people-centered payments

Green ideas: How sustainable finance benefits businesses

Empowering managers with data automation and integration

Employee benefit plan management: trustee vs. custodian

Protecting cash balances with sweep vehicles

Choosing your M&A escrow partner

Alternative investments: How to track returns and meet your goals

OCIO: An expanding trend in the investment industry

Delivering powerful results with SWIFT messaging and services

Tech lifecycle refresh: A tale of two philosophies

Sophisticated investors reduce costs with block trading

Understanding the role of authorized participants in exchange-traded funds

Optimizing treasury management

Why Bond Issuers Should Consider a Successor Trustee

Automating healthcare revenue cycle

Changes in credit reporting and what it means for homebuyers

What’s the difference between Fannie Mae and Freddie Mac?

Look to your custodian in times of change

Tapping into indirect compensation to recruit foreign talent

Why other lenders may be reaching out to your employees

How institutional investors can meet demand for ESG investing

Sustainability + mobility: Trends and practical considerations

CRE trends

A checklist for starting a mobility program review

Assisting transferees in a high mortgage interest rate environment

Mortgage buydowns and subsidies in today’s talent-focused relocation policies

Managing complex transactions: what your corporate trustee should be doing

Manufacturing: 6 supply chain optimization strategies

High-cost housing and down payment options in relocation

Why retail merchandise returns will be a differentiator in 2022

Technology Financing

Digital processes streamline M&A transactions

4 benefits of independent loan agents

Save time with mobile apps for business finances

At your service: outsourcing loan agency work

Middle-market direct lending: Obstacles and opportunities

How RIAs can embrace technology to enhance personal touch

Best practices for optimizing the tech lifecycle

What corporate treasurers need to know about Virtual Account Management

Work flexibility crucial as municipalities return to office

An asset manager’s secret to saving time and money

Overcoming the 3 key challenges of a lump sum relocation program

Treasury management innovations earn Model Bank awards

Crypto + Relo: Mobility industry impacts

For today's relocating home buyers, time and money are everything

Webinar: CRE Digital Transformation – Balancing Digitization with cybersecurity risk

How to sell your business without emotions getting in the way

Empowering team members

5 steps to take before transitioning your business

10 tips on how to run a successful family business

Quit your job to start a business: How to save enough

Starting a business with a friend: How to talk about it

How I did it: Grew my business by branching out

The moment I knew I’d made it: The Cheesecakery

Making a ‘workout’ work out as a business

Streamline operations with all-in-one small business financial support

How a bright idea became a successful business (in Charlotte, North Carolina)

Making the leap from employee to owner

Mapping out success for a small-business owner

Checklist: What you’ll need for your first retail pop-up shop

How mobile point of sale (mPOS) can benefit your side gig

How one organization is funding equity in the Chicago area

Business tips and advice for Black entrepreneurs

Staying organized when taking payments

Key considerations for online ordering systems

How does an electronic point of sale help your business keep track of every dime?

Tools that can streamline staffing and employee management

How to identify what technology is needed for your small business

Planning for restaurant startup costs and when to expect them

How a 13-year-old created a clothing line that reflects her passions

Starting a business? Follow these steps

Talent acquisition 101: Building a small business dream team

Make your business legit

7 tips to help grow your business after launch

How to fund your business without using 401(k) savings

How I did it: Turned my side hustle into a full-time job

Costs to consider when starting a business

The different types of startup financing

How to test new business ideas

How to get started creating your business plan

What is needed to apply for an SBA loan

How to establish your business credit score

The role of ethics in the hiring process

8 ways to increase employee engagement

The costs of hiring a new employee

How to reward employees and teams who perform well

How to hire employees: Employee referral vs. external hiring

Give a prepaid rewards card for employee recognition

5 steps for creating an employee recognition program

Tips for realtors to help clients get their homeownership goals back on track

Small business growth: 6 strategies for scaling your business

Healthcare marketing: How to promote your medical practice

Checklist: Increase lead generation with website optimization

5 affordable small business marketing ideas when you have no budget

Why ecommerce for small business strategy is integral

Opening a second location? Cloud-based POS is key to a smooth unveiling

Do you have the best Point of Sale for an internet outage?

4 restaurant models that aren’t dine-in

Omnichannel retail: 4 best practices for navigating the new normal

Is your restaurant Google-friendly?

How business owners are managing during the supply chain crisis

How small businesses are growing sales with online ordering

4 steps that give your business an SEO boost

Email marketing: 10 mistakes to avoid

What you should know about licensing agreements

How to expand your business: Does a new location make sense?

Essential marketing tools for any business

3 simple brand awareness tips for your business

How a small business owner is making the workplace work for women

5 principles for avoiding ethics pitfalls on social media

5 tips for helping employees raise ethics concerns

The growing importance of a strong corporate culture

Rethinking common time management tips

How small business owners can budget for the holiday season

Why credit cards should be the first choice for business payments

4 small business trends that could change the way you work

Common small business banking questions, answered

3 signs it’s time for your business to switch banks

Webinar: Leading through uncertainty: CFO Insights Executive Roundtable

7 uncommon recruiting strategies that you may not have tried yet

How increased supply chain visibility can combat disruptors

6 common financial mistakes made by dentists (and how to avoid them)

Unexpected expenses: 5 small business costs to know and how to finance them

Strengthen your brand with modern POS technology

Technology strategies to complement your business plan

Business credit card support

Business credit card 101

Meet your business credit card support team

How to apply for a business credit card

What kind of credit card does my small business need?

Do I need a credit card for my small business?

How jumbo loans can help home buyers and your builder business

When to consider switching banks for your business

How to choose the right business checking account

5 tips to help you land a small business loan

How to choose the right business savings account

5 questions business owners need to consider before taking out a loan

Does your side business need a separate bank account?

Leverage credit wisely to plug business cash flow gaps

How to establish your business credit score

The essential business tips for tax deductions

How to make the most of your business loan

How to accept credit cards online

Do you need a business equipment loan?

Break free from cash flow management constraints

5 tips for managing your business cash flow

5 ways a business credit card program can grow your business

How Everyday Funding can improve cash flow

Building a business with a great product and a greater purpose

3 ways POS data analysis can help define your brand

How running a business that aligns with core values is paying off

Meet the Milwaukee businessman behind Funky Fresh Spring Rolls

Improve online presence your business

When small business and community work together
How a family-owned newspaper is serving its community

How tenacity brought Taste of Rondo to life

How Gentlemen Cuts helps its community shine

How Lip Esteem is empowering women

Community behind Elsa’s House of Sleep

Honey Luxury Beauté: growing a side project into an eye-catching beauty business

How Shampoo’ed is transforming hair and inspiring entrepreneurs

The San Francisco bridal shop that’s been making memories for 30 years

How Al’s Breakfast is bringing people together

In a digital world, Liberty Puzzles embraces true connection

Celebrity Cake Studio’s two decades of growth and success

How four women pivoted amidst a pandemic

How a travel clothing retailer is staying true to its brand values

How to build a content team

3 ways to gain loyalty with your customers

Use this one simple email marketing tip to increase your reach

How (and why) to get your business supplier diversity certification

5 ways to build your business through community engagement

12 ways to reduce your taxable income

Multigenerational household financial planning strategies

Major purchases: How to pay for big ticket items

LGBTQ+ financial planning tips

12 financial goal examples to explore

Financial fitness quiz

Key components of a financial plan

Do I need a financial advisor?

5 financial goals for the new year

How to track expenses

How to manage your finances when you're self-employed

Good debt vs. bad debt: Know the difference

Good money habits: 6 common money mistakes to avoid

How to prepare for a recession: 6 steps to take

7 beneficiary designation mistakes to avoid

Gifting money to adult children: Give now or later?

Reviewing your beneficiaries: A 5-step guide

Estate planning checklist: 8 steps to secure your legacy

How to talk about money with your family

Financial steps to take after the death of a spouse

6 tips for trust fund distribution to beneficiaries

Preparing for an empty nest: Financial and lifestyle tips

Retirement quiz: How ready are you?

How to build wealth at any age

Retirement plan options for the self-employed

IRA vs. 401(k): What's the difference?

Retirement advice: How to retire happy

Social Security benefits questions and answers

Key milestone ages as you near and start retirement

Retirement income planning: 4 steps to take

Retirement savings by age

Webinar: Why planning for retirement should start now

Preparing for retirement: 8 steps to take

Comparing term vs. permanent life insurance

Healthcare costs in retirement: Are you prepared?

How much life insurance do I need?
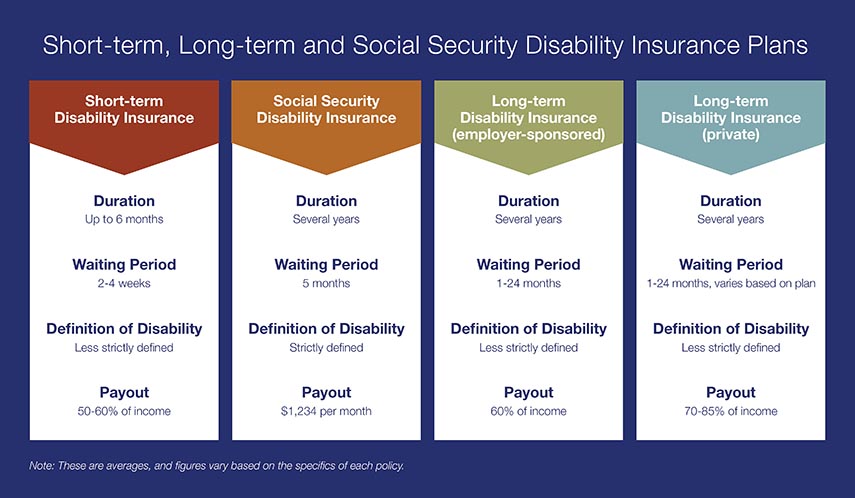
Is your employer long term disability insurance enough?

8 steps to choosing a health insurance plan

What is Medicare? Understanding your coverage options

7 things to know about long-term care insurance

How to keep your assets safe

How I did it: Switched career paths by taking an unexpected pivot

How I did it: Transitioned from the military to a private sector career

How I did it: Joined a board of directors

5 tips for being a great board member

Transitioning from the military to the civilian workforce

Military spouse’s guide to navigating your career

Webinar build career best foot forward

Achieving their dreams through a pre-apprenticeship construction program

How to search for jobs (and interview) in a virtual job market

Working after retirement: Factors to consider

The Anaheim Ballet: Making a difference through dance

Why year-round giving is important

6 ways to teach your kids about giving

4 steps to finding a charity to support

Freelancer's tax guide: Simplify your filing process

How to be prepared for tax season as a gig worker

Tips and tools for tax season and beyond

Year end tax planning tips

Should I itemize my taxes?

10 ways your income and assets can affect your taxes

A guide to tax diversification in investing

Economic forecast: 3 things to know for 2024's 2nd half

Bull vs. bear market: What do they mean for you?

Robo advisors vs. financial advisors: How are they different?

Start a Roth IRA for kids

Investing myths: Separating fact from fiction in investing

What Is a 401(k)?

ETF vs. mutual fund: What’s the difference?

How does an IRA work?

What are alternative investments?

4 times to consider rebalancing your portfolio

Effects of inflation on investments

How much money do I need to start investing?

7 diversification strategies for your investment portfolio

Saving vs. investing: What's the difference?

4 major asset classes explained

Why compound annual growth matters

How to start investing: A beginner’s guide

5 questions to help you determine your investment risk tolerance

Do your investments match your financial goals?

Investment strategies by age

How to roll over your 401(k)

Non-retirement investing: Investment options outside of retirement accounts

How do interest rates affect investments?

What types of agency accounts are available for investors?

How to budget 101: 6 strategies to try

How to Adult: 7 tax terms and concepts you should know

How to Adult: 5 ways to track your spending

Tips for navigating a medical hardship when you’re unable to work

3 steps to prepare for a medical emergency

LGBTQ+ family planning: 3 questions to ask employers

LGBTQ+ adoption 101: What prospective parents should know

Legal protections for growing LGBTQ+ families

11 essential things to do before baby comes

Webinar: Uncover the cost: Starting a family

Preparing for adoption and IVF

How to plan and save for adoption and in vitro fertility treatment costs

Checklist: 10 questions to ask your home inspector

Closing on a house checklist for buyers

Handling the finances of someone who has died: Terms and definitions

Resources for managing financial matters after an unexpected death

What you need to know as the executor of an estate

When your spouse has passed away: A three-month financial checklist

What documents do you need after a loved one dies?

Simple steps to be ready for a natural disaster

Checklist: financial recovery after a natural disaster

Rebuilding finances after a natural disaster

How does money influence your planning?

College budgeting: When to save and splurge

Webinar: 11 insider tips for student debt

U.S. Bank Student Scholarship

Student checklist: Preparing for college

6 questions students should ask about checking accounts

Uncover the cost of a college diploma

How to save money in college: easy ways to spend less

How to gain financial independence from your parents

The A to Z’s of college loan terms

Co-signing 101: Applying for a loan with co-borrower

Practical money skills and financial tips for college students

How to build credit as a student

5 things to know before accepting a first job offer

Learn to spot and protect yourself from common student scams

How I did it: Paid off student loans
Bank Notes: College cost comparison

Four ways to make a strong resume for your first real job

Tips to earn that A+ in back-to-school savings

7 ways to teach your children to be scam-savvy

How to prevent fraud

Outsmart tax scams and keep your finances safe

Lessons learned from experiencing a scam

Keep your finances safe and secure: Essential tips for preventing check fraud

Webinar: How to stay safe from cyberfraud

How to avoid student loan scams

Protecting elderly parents’ finances: 6 steps to follow when managing their money

4 ways to outsmart your smart device

Banking basics: Avoiding fraud and scams
How to spot an online scam

Money muling 101: Recognizing and avoiding this increasingly common scam

Annual insurance review checklist

What you need to know about identity theft

What is financial fraud?

From LLC to S-corp: Choosing a small business entity

5 tips for seniors to stay a step ahead of schemers

Recognize. React. Report. Don't fall victim to financial exploitation

Recognize. React. Report. Caregivers can help protect against financial exploitation

Webinar: U.S. Bank asks: Are you safe from fraud?

Is online banking safe?

How-to guide: What to do if your identity is stolen

How you can prevent identity theft

8 tips and tricks for creating and remembering your PIN

How to avoid being the victim of a digital payments scam

Helping Gen Z build financial confidence

Short- and Long-Term Financial Goals for Every Life Stage

How your taxes can change after a major life event

Get back on track with your New Year’s financial resolutions

What to do with your tax refund or bonus

Live your money values in 2024

Loud budgeting explained: Amplify your money talk

How to set financial goals you will keep

Financial goals for 2024 a 12-month planning guide

How to save for a dream vacation

Tips for talking about money when friends earn more

How new parents can prepare for the costs of a new child

How to save more money in 2024

Building confidence in your finances and career

How to financially prepare for pet costs

Pros and cons of a personal line credit

3 tips for saving money when moving to a new home

5 ways to maximize your garage sale profits

Tips for handling rising costs from an Operation HOPE Financial Wellbeing coach

What is a Certificate of Deposit? And what to know before opening an account

What does FDIC mean?

Is raising backyard chickens a good idea financially?

3 financial tools to help automate your finances

5 things to deinfluence in your finances

3 ways to keep costs down at the grocery store (and make meal planning fun)

5 tips for creating (and sticking to) a holiday budget

Make holiday gift giving easier in a digital world

Should you buy now, pay later?

Financial checklist: Preparing for military deployment

How to financially prepare for a military PCS

Planning self-care moments that matter (and how to finance them)

Friction: How it can help achieve money goals

5 things to consider when deciding to take an unplanned trip

Stay committed to your goals by creating positive habits

An eco friendly debit card with roots in Haiti

Creating positive money habits

Finding a side gig to fund your goals

How I kicked my online shopping habit and got my spending under control

Growing your savings by going on a ‘money hunt’

Working with an accountability partner can help you reach your goals

The banking app you need as a new parent

Why a mobile banking app is a ‘must have’ for your next vacation

How to decide when to shop local and when to shop online

A who’s who at your local bank

Webinar: 5 myths about emergency funds

How I did it: Learned to budget as a single mom

Your guide to starting a job: Resources to help along the way

Your 5-step guide to financial planning

How to set yourself up for success in your first job

5 myths about emergency funds

Financial Wellness Assessment

How to stay positive when searching for a job

Banking basics: How to start saving

Webinar: Common budget mistakes (and how to avoid them)

Does your savings plan match your lifestyle?

Mobile banking tips for smarter and safer online banking

Uncover the cost: Wedding

Uncover the cost: International trip

What military service taught me about money management

Are savings bonds still a thing?

Tips to overcome three common savings hurdles

Booming in the gig economy: A new chapter leveraging 45 years of experience

Adulting 101: How to make a budget plan

How having savings gives you peace of mind

Helpful tips for safe and smart charitable giving

Personal loans first-timer's guide: 7 questions to ask

3 awkward situations Zelle can help avoid

Allowance basics for parents and kids

What’s your financial IQ? Game-night edition

Mindset Matters: How to practice mindful spending

How and when to ask for a raise

How to save money while helping the environment

How to choose the right rewards credit card for you

How can I help my student manage money?

Steer clear of overdrafts to your checking account

How to manage money in the military: A veteran weighs in

Things to know about the Servicemembers Civil Relief Act

You can take these 18 budgeting tips straight to the bank

3 tips for saving money easily

Save time and money with automatic bill pay

How to best handle unexpected expenses

Common unexpected expenses and three ways to pay for them

Stay on budget — and on the go — with a mobile banking app

Which is better: Combining bank accounts before marriage — or after?

Do you and your fiancé have compatible financial goals?

U.S. Bank asks: Transitioning out of college life? What’s next?
U.S. Bank asks: Do you know your finances?
U.S. Bank asks: Do you know what an overdraft is?

Personal finance for teens can empower your child

Is it time to get a shared bank account with your partner?

It's possible: 7 tips for breaking the spending cycle

How to save for a wedding

How can you pay bills online the right way?

Here’s how to create a budget for yourself

Don’t underestimate the importance of balancing your checking account

9 simple ways to save

7 steps to prepare for the high cost of child care

A passion for fashion: How this student works the gig economy
Earning in the gig economy: Gladys shares her story

By the numbers: The gig economy

Tips for working in the gig economy

How compound interest works

Dear Money Mentor: How do I set and track financial goals?

5 tips for parents opening a bank account for kids

5 reasons why couples may have separate bank accounts

Checking and savings smarts: Make your accounts work harder for you

Lost job finance tips: What to do when you lose your job

Money Moments: 3 smart financial strategies when caring for aging parents

Tips to raise financially healthy kids at every age

Money management guide to financial independence

First-timer’s guide to savings account alternatives

Money Moments: 8 dos and don’ts for saving money in your 30s

7 financial questions to consider when changing jobs

Tips and resources to help in the aftermath of a natural disaster

Myths vs. facts about savings account interest rates

30-day adulting challenge: Financial wellness tasks to complete in a month

5 tips to use your credit card wisely and steer clear of debt

Travel for less: Smart (not cheap) ways to spend less on your next trip

Money Moments: How to manage your finances after a divorce

Money Moments: 3 tips for planning an extended leave of absence

Overdrafts happen: Steps to get you back on track

What’s in your emergency fund?

Certificates of deposit: How they work to grow your money

P2P payments make it easier to split the tab

Essential financial resources and protections for military families

What you need to know about renting

Dear Money Mentor: How do I pick a savings or checking account?

Real world advice: How parents are teaching their kids about money

How to stop living paycheck to paycheck post-pay increase

Practical money tips we've learned from our dads

6 ways to spring clean your finances and save money year-round

Meet the student with a passion for science, helping others and reaching goals

What I learned from my mom about money

How to cut mindless spending: real tips from real people

Understanding guardianship and power of attorney in banking

How to increase your savings

Bank from home with these digital features

What financial advice would you give your younger self?

Military finance: How to create a family budget after military service

Managing money as a military spouse during deployment
How I saved $10,000 in just one year

Discovering your money personality can help you save

Tips on how couples can learn to agree about money

Your guide to smart money habits

Understanding your military GI Bill benefits

Webinar: How to pay for college

How grandparents can contribute to college funds instead of buying gifts

How to open and invest in a 529 plan

Using 529 plans for K-12 tuition

Your financial aid guide: What are your options?

Is a home equity loan for college the right choice for your student

Parent checklist: Preparing for college

How to apply for federal student aid through the FAFSA

What to consider before taking out a student loan

How I did it: Dug my way out of a five-figure student loan debt

Are you ready to restart your federal student loan payments?

Consolidating debts: Pros and cons to keep in mind

How to talk to your lender about debt

Which debt management technique is right for you?

Everything you need to know about consolidating debts

Managing debt

Best travel credit card perks for family vacations

5 tips to use your credit card wisely and steer clear of debt

5 steps to selecting your first credit card

How to use debt to build wealth

What’s a subordination agreement, and why does it matter?

Understanding the true cost of borrowing: What is amortization, and why does it matter?

7 steps to keep your personal and business finances separate

Know your debt-to-income ratio

How to pay off credit card debt

How to use credit cards wisely for a vacation budget

Your quick guide to loans and obtaining credit
Dear Money Mentor: How do I begin paying off credit card debt?

Checklist: 10 things to look for when touring a home

How to sell and buy a home at the same time

Mortgages after retirement: Here’s what to know

Dear Money Mentor: What is cash-out refinancing and is it right for you?

Home improvements with the best ROI

Overcoming high interest rates: Getting your homeownership goals back on track

How we did it: Converted to solar power

Is it cheaper to build or buy a house

PCS moving checklist for military spouses and families

For today's homebuyers, time and money are everything

Crypto + Homebuying: Impacts on the real estate market

Should you buy a house that’s still under construction?

How I did it: Bought my dream home using equity

Buying a home Q&A: What made three homeowners fall in love with their new home

House Hacks: How buying an investment property worked as my first home

Starting your homebuying journey

Managing the impacts of appraisal gaps in a hot housing market

How I did it: Built living spaces to support my family

Spring cleaning checklist for your home: 5 budget-boosting tasks

Bringing economic opportunity to underserved communities one home at a time

Community activist achieves dream of homeownership

Saving for a down payment: Where should I keep my money?

Your guide to breaking the rental cycle

DIY home projects 101: tips from a first-timer

Checklist: 6 to-dos for after a move

What are conforming loan limits and why are they increasing

Military homeownership: Your guide to resources, financing and more

Uncover the cost: Building a home

How I did it: Bought a home without a 20 percent down payment

The lowdown on 6 myths about buying a home

Home buying myths: Realities of owning a home

4 ways to free up your budget (and your life) with a smaller home

Get more home for your money with these tips

Money Moments: Tips for selling your home

Money Moments: How to finance a home addition

How I did it: My house remodel

Are professional movers worth the cost?

First-time homebuyer’s guide to getting a mortgage

Dear Money Mentor: When should I refinance a mortgage?

Beyond the mortgage: Other costs for homeowners

Quiz: How prepared are you to buy a home?

What is a mortgage?

Building a dream home that fits your life

10 ways to increase your home’s curb appeal

10 questions to ask when hiring a contractor

5 things to avoid that can devalue your home

How you can take advantage of low mortgage rates

What is an escrow account? Do I have one?

Is it the right time to refinance your mortgage?

What to know when buying a home with your significant other

What is refinancing a mortgage?

These small home improvement projects offer big returns on investment

Should you get a home equity loan or a home equity line of credit?

Mortgage basics: What’s the difference between interest rate and annual percentage rate?

Mortgage basics: What is refinancing, and is it right for you?

Mortgage basics: Prequalification or pre-approval – What do I need?

Mortgage basics: How much house can you afford?
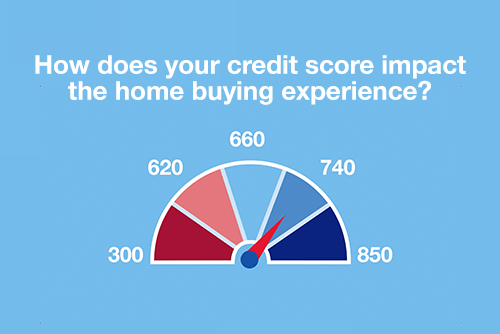
Mortgage basics: How does your credit score impact the homebuying experience?
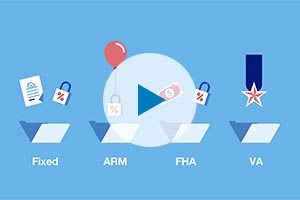
Mortgage basics: Finding the right home loan for you

Mortgage basics: Buying or renting – What’s right for you?

Mortgage basics: 3 key steps in the homebuying process

Is a home equity line of credit (HELOC) right for you?

How to use your home equity to finance home improvements

How does a home equity line of credit (HELOC) work?

How do I prequalify for a mortgage?

Home equity: Small ways to improve the value of your home

Can you take advantage of the dead equity in your home?

8 steps to take before you buy a home

6 questions to ask before buying a new home

4 questions to ask before you buy an investment property

10 uses for a home equity loan

Uncover the cost: Home renovation

How to request a credit limit increase

What applying for store credit card on impulse could mean

Improving your credit score: Truth and myths revealed

How to spot a credit repair scam

6 essential credit report terms to know

5 unique ways to take your credit card benefits further

How to maximize your credit card rewards

Myth vs. truth: What affects your credit score?

Test your loan savvy

Decoding credit: Understanding the 5 C’s

Credit: Do you understand it?

How to build and maintain a solid credit history and score

Should you give your child a college credit card?

U.S. Bank asks: What do you know about credit?

What types of credit scores qualify for a mortgage?

What is a good credit score?

Credit score help: Repairing a bad credit score

How to improve your credit score

Common questions about electric vehicles (EVs)

What to keep in mind when buying a used car from a private seller

I own two electric vehicles. Here’s what I’ve learned about buying and driving EVs.

How I decided that buying an RV was worth it for me

Car shopping: Buying versus leasing your next vehicle

Take the stress out of buying your teen a car

How to winterize your vehicle

Questions to ask before buying a car

What you should know about buying a car

When to and benefits of refinancing a car loan

How to choose the best car loan for you

