
The latest on cybersecurity: Mobile fraud and privacy concerns

How a Health Savings Account (HSA) can benefit your retirement plan

Liquidity management: A renewed focus for European funds

Cryptocurrency custody 6 frequently asked questions

3 tips to maintain flexibility in supply chain management

5 questions you should ask your custodian about outsourcing

Insource or outsource? 10 considerations

10 ways a global custodian can support your growth

The benefits of a full-service warehouse custodian

Colleges respond to student needs by offering digital payments

6 timely reasons to integrate your receivables

Benefits of billing foreign customers in their own currency

Improve government payments with electronic billing platforms

Third-party vendor risk: protecting your company against cyber threats

Hospitals face cybersecurity risks in surprising new ways

Authenticating cardholder data reduce e-commerce fraud

Post-pandemic fraud prevention lessons for local governments

Webinar: Robotic process automation

Risk management strategies for foreign exchange hedging

Proactive ways to fight vendor fraud

Webinar: CRE technology trends

5 Ways to protect your government agency from payment fraud

Avoiding the pitfalls of warehouse lending

Fight the battle against payments fraud

Fraud prevention checklist

Cybercrisis management: Are you ready to respond?

Why Know Your Customer (KYC) — for organizations

The password: Enhancing security and usability

How to improve your business network security

Government agency credit card programs and PCI compliance

Cybersecurity – Protecting client data through industry best practices

BEC: Recognize a scam

Meeting healthcare strategy goals with electronic patient refunds

Standardizing healthcare payments

Consolidating payments for healthcare systems

Access, flexibility and simplicity: How governments can modernize payments to help their citizens

Modernizing fare payment without leaving any riders behind

Tap-to-pay: Modernizing fare payments pays off for transit agencies and riders

Webinar: Approaching international payment strategies in today’s unpredictable markets.

How real-time inventory visibility can boost retail margins

Escheatment resources: Reporting deadlines for all 50 states

Payment industry trends that are the future of POS

White Castle optimizes payment transactions

ABCs of APIs: Drive treasury efficiency with real-time connectivity

Managing the rising costs of payment acceptance with service fees

Three healthcare payment trends that will continue to matter in 2022

Want AP automation to pay both businesses and consumers?

Webinar: CSM corporation re-thinks AP

Increase working capital with Commercial Card Optimization

How to improve digital payments security for your health system

3 benefits of integrated payments in healthcare

Top 3 ways digital payments can transform the patient experience

Automate accounts payable to optimize revenue and payments

Automate escheatment for accounts payable to save time and money

Ways prepaid cards disburse government funds to the unbanked

Webinar: AP automation for commercial real estate

Understanding and preparing for the new payment experience

Safeguarding the payment experience through contactless

COVID-19 safety recommendations: Are you ready to reopen?

Higher education and the cashless society: Latest trends

5 winning strategies for managing liquidity in volatile times

3 ways to make practical use of real-time payments

The surprising truth about corporate cards

The future of financial leadership: More strategy, fewer spreadsheets

4 benefits to paying foreign suppliers in their own currency

Restaurant surveys show changing customer payment preferences

Unexpected cost savings may be hiding in your payment strategy

Digital trends poised to reshape hotel payments

Enhancing the patient experience through people-centered payments

Protecting cash balances with sweep vehicles

Alternative investments: How to track returns and meet your goals

Automating healthcare revenue cycle

Manufacturing: 6 supply chain optimization strategies

Overcoming the 3 key challenges of a lump sum relocation program

Webinar: CRE Digital Transformation – Balancing Digitization with cybersecurity risk

Streamline operations with all-in-one small business financial support

Checklist: What you’ll need for your first retail pop-up shop

How mobile point of sale (mPOS) can benefit your side gig

Small business growth: 6 strategies for scaling your business

Healthcare marketing: How to promote your medical practice

Rethinking common time management tips

6 common financial mistakes made by dentists (and how to avoid them)

How to apply for a business credit card

How jumbo loans can help home buyers and your builder business

How to accept credit cards online

How Everyday Funding can improve cash flow

Healthcare costs in retirement: Are you prepared?
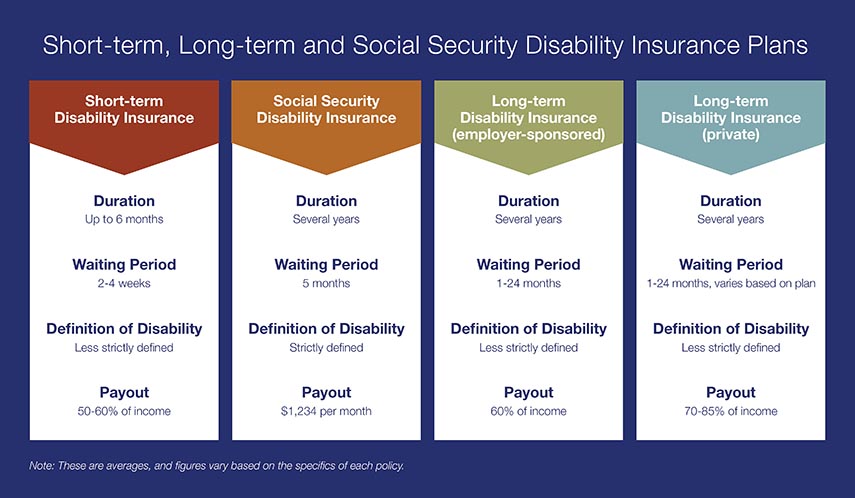
Is your employer long term disability insurance enough?

What is Medicare? Understanding your coverage options

7 things to know about long-term care insurance

How to keep your assets safe

3 steps to prepare for a medical emergency

How to plan and save for adoption and in vitro fertility treatment costs

When your spouse has passed away: A three-month financial checklist

What documents do you need after a loved one dies?

How to save money in college: easy ways to spend less

Learn to spot and protect yourself from common student scams

7 ways to teach your children to be scam-savvy

Keep your finances safe and secure: Essential tips for preventing check fraud

Webinar: How to stay safe from cyberfraud

4 ways to outsmart your smart device
How to spot an online scam

Money muling 101: Recognizing and avoiding this increasingly common scam

What is financial fraud?

How-to guide: What to do if your identity is stolen

How you can prevent identity theft

Why a mobile banking app is a ‘must have’ for your next vacation

Mobile banking tips for smarter and safer online banking

3 awkward situations Zelle can help avoid

Dear Money Mentor: How do I set and track financial goals?

7 financial questions to consider when changing jobs

P2P payments make it easier to split the tab
Dear Money Mentor: How do I begin paying off credit card debt?

